Ryan Pickren — the cyber security student and former Amazon Web Services security engineer that was able to hack his way into the iPhone camera in 2019 — is back with a Mac Safari exploit that allowed him to access the victims’ online accounts and their webcam.
Thanks to Apple’s nearly $2 million CAD bug bounty program, Pickren walked away with a $100,000 bounty for reporting the bug (largest payout to date) and is now sharing information about the exploit.
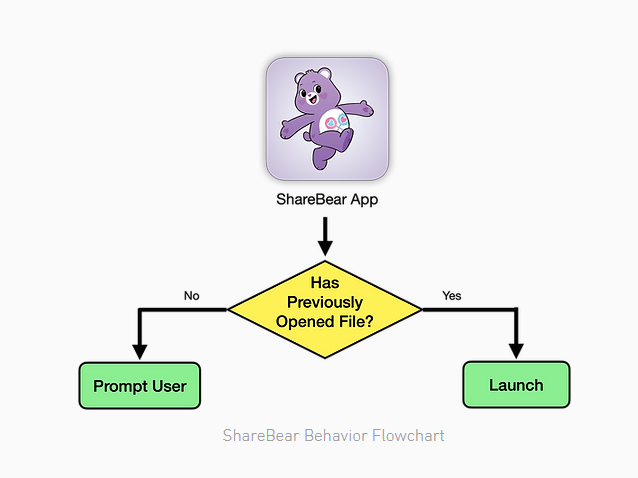
According to Pickren, the vulnerability lies in an iCloud sharing app called ShareBear. To get into someone’s Mac, the exploiter would need to share a file with the potential victim, and since the victim’s Mac would remember that it accepted the file, it would automatically be granted permission.
This file is stored remotely, and the exploiter has full access to edit the file’s content and turn it into malware. Since the potential victim’s Mac already recognizes the file and has granted permission to it, the exploiter can execute the file without the unsuspecting potential victim having to allow the action.
“In essence, the victim has given the attacker permission to plant a polymorphic file onto their machine and the permission to remotely launch it at any moment. Yikes. Agreed to view my PNG file yesterday? Well today it’s an executable binary that will be automatically launched whenever I want,” reads Pickren’s blog post.
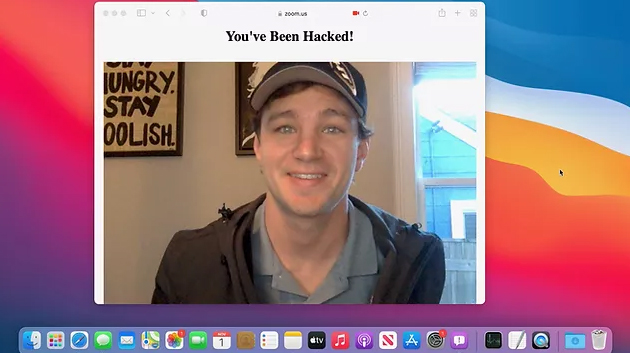
Once Pickren has complete access to execute the malware whenever he wants, he can access the infected Mac’s saved online accounts and even turn on/off its camera and microphones, albeit after tricking macOS’ Gatekeeper. Pickren explains it in great detail here.
Pickren reported the exploit to Apple in July 2021, and the issue has was patched earlier this month.
Image credit: Ryan Pickren
Source: Ryan Pickren
MobileSyrup may earn a commission from purchases made via our links, which helps fund the journalism we provide free on our website. These links do not influence our editorial content. Support us here.