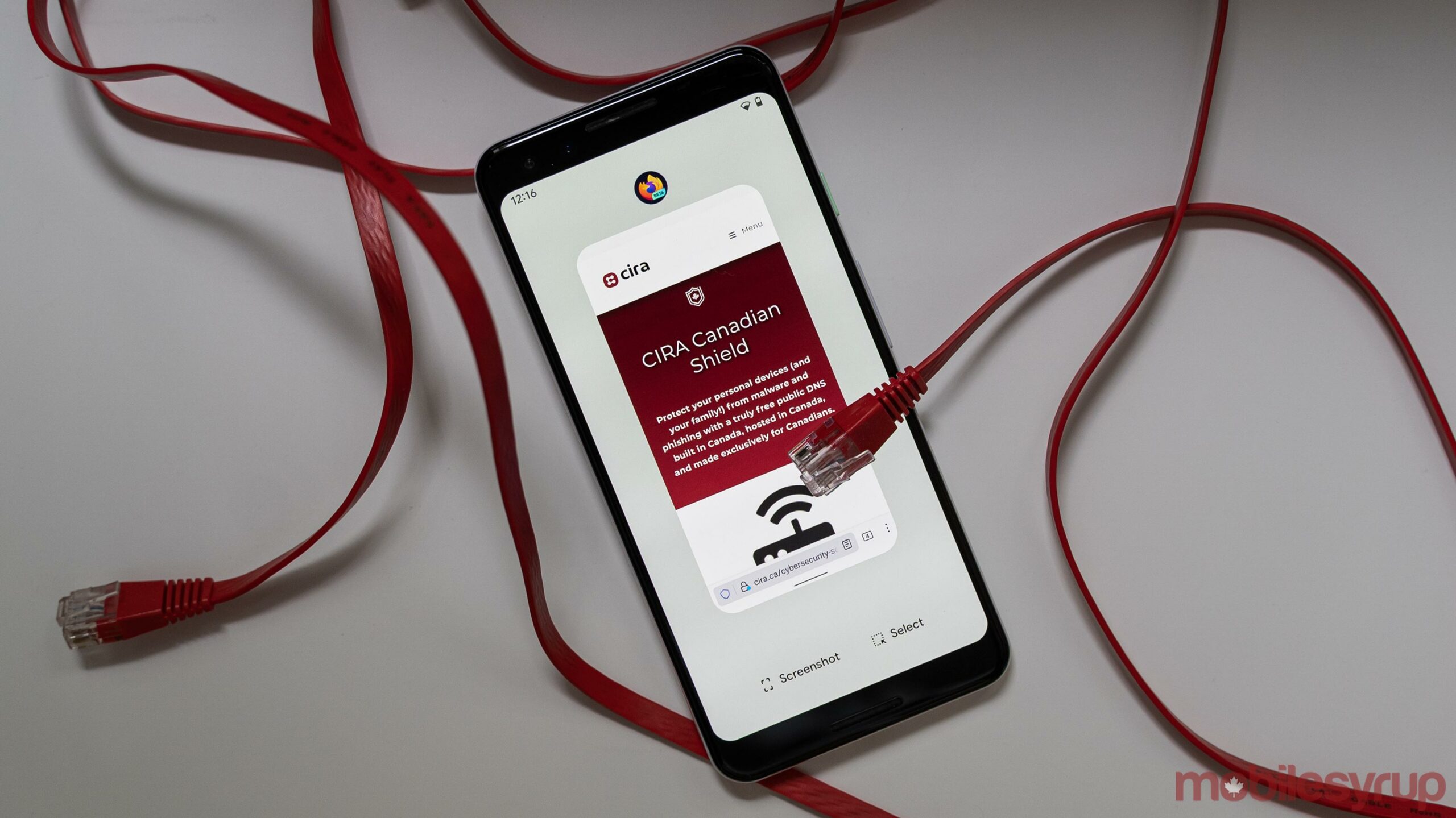
Mozilla and the Canadian Internet Registration Authority (CIRA) have teamed up to add the organization’s ‘Canadian Shield‘ as the default DNS over HTTPS (DoH) provider for the Firefox browser in Canada.
In a blog post, Mozilla explained that starting July 20th, about one percent of Canadian Firefox users will see CIRA set as the default DoH provider. Over the next few months, the percentage will increase, with the goal of hitting 100 percent of Canadian Firefox users by late September 2021. However, those running a preview build of Firefox may already see CIRA set as the DoH provider — I use Firefox’s Nightly variant on my PC, and it had switched to CIRA DoH when I checked the setting this morning (you can learn how to check DoH settings below).
Further, a CIRA press release notes that Firefox will use Canadian Shield’s ‘Private’ feed by default. Canadians will have the option to switch to other Canadian Shield options, such as ‘Public’ for malware and phishing protection or ‘Family’ that includes blockers for pornographic content.
CIRA’s Canadian Shield is also available on mobile via a smartphone app, on Windows or Mac through system configurations or at the router level. Those interested can learn more about Canadian Shield here, or get started using the platform here.
What is DNS over HTTPS?
As a refresher, DoH is a method of protecting DNS requests by encrypting them and sending them over the secure HTTPS protocol instead of HTTP by default. DNS, or Domain Name System, is effectively the phone book of the internet — when people want to go to a website, such as ‘www.mobilesyrup.com,’ they type that domain name into their browser. The browser then uses a DNS service to look up the Internet Protocol (IP) address for that domain to connect the device to the website.
By default, most people’s internet service provider (ISP) handles DNS. However, since DNS requests are, by default, unencrypted, this can be problematic. First, unencrypted DNS requests can be intercepted by malicious actors, allowing someone to tamper with browsing activity. While DoH can help protect users from that, it doesn’t necessarily help with the other issue: data privacy.
DNS requests can include a lot of sensitive information about users, such as browsing activity. Whatever DNS resolver handles DNS requests from your computer will have access to that information. Moreover, most places don’t limit what companies can do with that data. In other words, DNS resolvers can collect the information and sell, share or license it to other groups.
DoH can protect DNS requests in transit, but when they arrive at the resolver, it can still gather the data. Instead, users must proactively protect themselves by selecting a DNS resolver they trust. That can be done at various levels — many routers have a DNS option that would apply to all traffic through a network, most computers and phones can set a system-wide DNS and browsers often have DNS or DoH options too.
As an aside, Google got into some hot water in 2019 over a plan to enable DoH settings for Chrome users. American ISPs raised concerns that Google would move Chrome users to the search giant’s DNS service, cutting ISPs out of a likely lucrative method of gathering data on customers’ browsing activities. Google later clarified that it only planned to enable DoH for users if their DNS resolver supported the feature, and that it wouldn’t change users’ DNS settings.
It appears ISPs haven’t raised similar concerns with Mozilla’s DoH approach in Firefox, likely because Firefox doesn’t have nearly as large of a user base as Chrome.
A Mozilla program helps ensure people use trustworthy DNS resolvers
Mozilla has been working to solve that second DNS problem through its Trusted Recursive Resolver (TRR) program. Through TRR, Mozilla aims to standardize data collection and retention requirements for DNS resolvers. Companies that partner with Mozilla through TRR must meet the company’s data policies, which include:
- Limiting data: Mozilla requires that DNS providers only use data “for the purpose of operating the service,” can’t keep data for more than 24 hours and cannot sell, share or license the data to other parties.
- Transparency: Mozilla requires DNS providers to publish public privacy notices that document what data they retain and how they use the data.
- Blocking and modification: Mozilla requires DNS resolvers not to block, filter, modify or provide inaccurate responses unless strictly required by law to do so. However, Mozilla does allow DNS blocking and filtering when users specifically opt-in to it through features like parental controls.
As part of Mozilla adding CIRA’s Canadian Shield to Firefox by default for Canadians, the company also added CIRA to its TRR program. CIRA joins other DNS providers, including Cloudflare, NextDNS and Comcast (U.S. only).
What CIRA in Firefox means for Canadians
Ultimately, this change should improve privacy by default for Canadians that use Firefox. Mozilla enabled DoH by default for U.S. users in February 2020 and now Canadians will also have DoH by default as well. For the less tech-savvy users out there, the change should improve their privacy when browsing the web with Firefox through DoH.
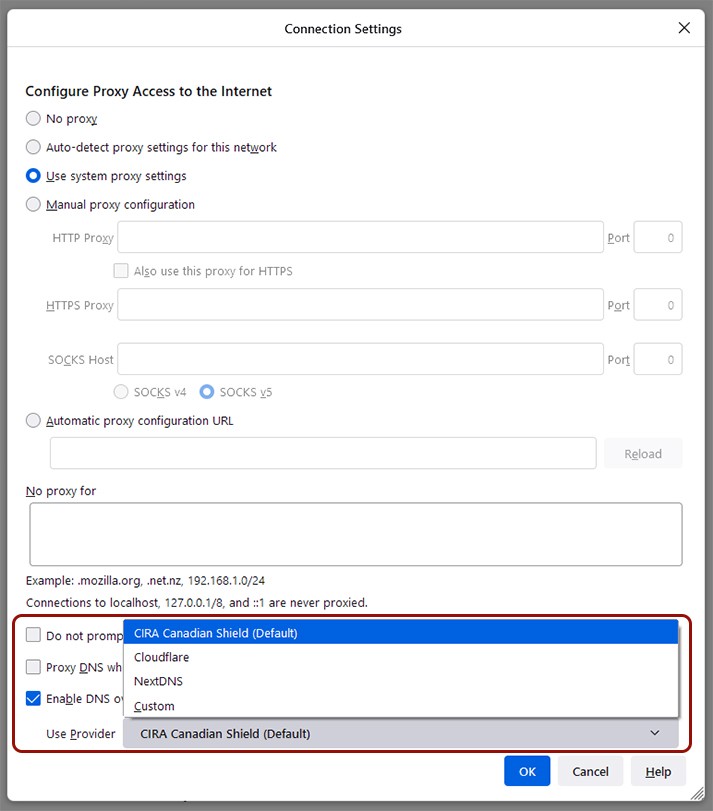
However, some more tech-savvy users and privacy enthusiasts may prefer to use a DNS resolver of their choice over CIRA. Thankfully, Firefox still lets you customize DoH settings. To so, click the three-line menu button in the top-right corner > Settings > General > scroll to ‘Network Settings’ at the bottom and click the ‘Settings’ button > check ‘Enable DNS over HTTPS’ and use the drop-down menu to select a provider. Unfortunately, at the time of writing, Firefox’s mobile browsers didn’t have a DoH option, but those who want to use CIRA Canadian Shield can download the mobile app instead.
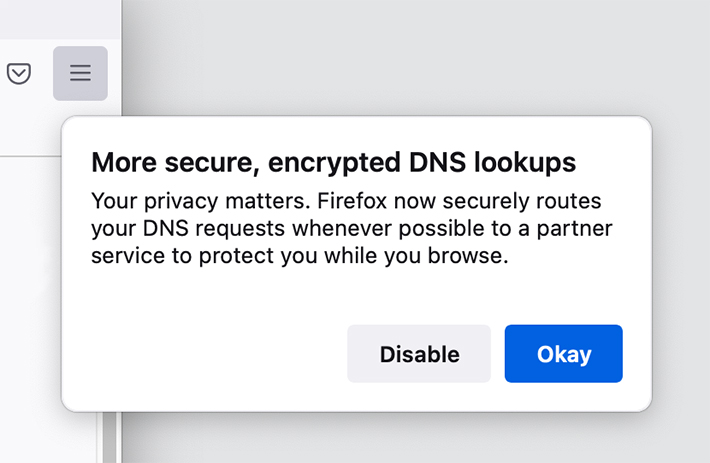
Currently, Firefox offers three DoH options for Canadians — Cloudflare, NextDNS or a custom option is someone wants to set up their own DoH settings. In the future, Canadians will see CIRA Canadian Shield in the menu as well. As the option rolls out, Canadians should see a pop-up message in Firefox letting them know about DoH and giving them an option to opt-out before the browser implements the change. The above image shows what the pop-up looks like.
Those interested can learn more about Mozilla’s TRR program here and Firefox’s DoH settings via this FAQ page. Those interested in learning more about CIRA Canadian Shield can do so here.
MobileSyrup may earn a commission from purchases made via our links, which helps fund the journalism we provide free on our website. These links do not influence our editorial content. Support us here.


