It looks like the days of Nintendo DS flashcards have returned.
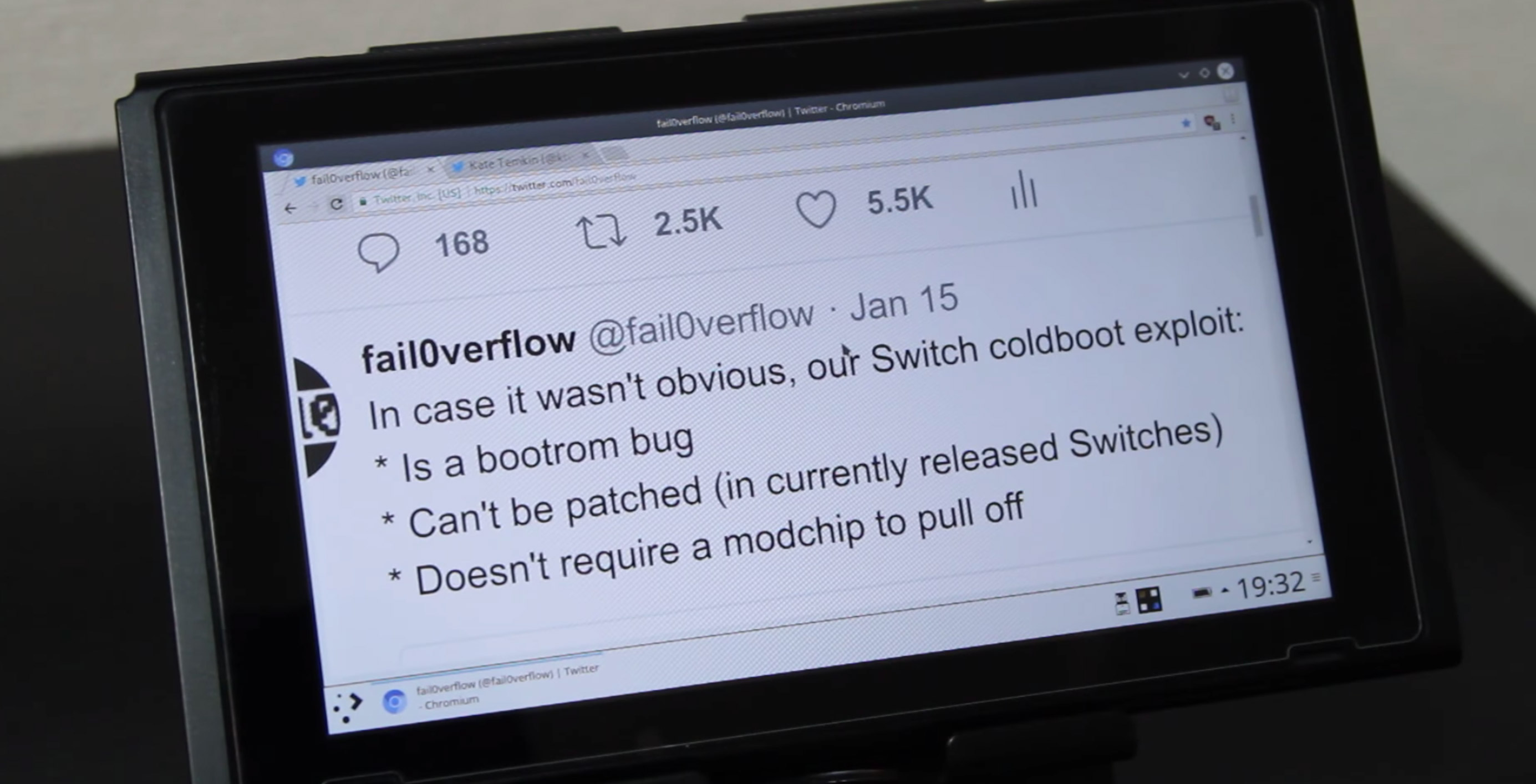
Following a complete dump of the Nintendo Switch’s boot ROM, two exploits for the console have been dropped over the last 24 hours. Both of these hacks relate to a hardware exploit and can’t be patched by Nintendo, according to the groups behind the exploits.
Reminder: ShofEL2 cannot be patched in existing units (it will work on *any* firmware, past or future), it allows full access (all keys and secrets), and it is completely undetectable by normal software. You can dual boot Linux and Switch OS with impunity. https://t.co/bqpmqBWkem
— fail0verflow (@fail0verflow) April 24, 2018
The only way for Nintendo to patch the hack would be to alter the Nividia Tegra X1’s architecture — the processor that powers the Switch — in order to remove the ROM exploit. This means that homebrew code, a full touch-enabled version of Linux and of course, even pirated commercially released games at some point, will soon be compatible with the console.
The exploit was first uncovered by hackers ‘Fail0verflow’ with the group’s ShofEL2 release, as well as the Fusée Gelée hack from Kate Temik and the team at ReSwitched. Both hackers claim that the exploit was disclosed to Google, Nintendo and Nvidia a number of months ago, before being released recently. Fail0verflow opted to push out the exploit because the Switch’s boot ROM dump leaked.
The video above shows off a touchscreen version of Linux running on the console.
“Choosing whether to release an exploit or not is a difficult choice. Given our experiences with past consoles, we’ve been wary of releasing vulnerability details or exploits for fear of them being used primarily for piracy rather than homebrew,” writes theFail0verflow on its official website.
“That said, the Tegra bootrom bug is so obvious that multiple people have independently discovered it by now; at best, a release by other homebrew teams is inevitable, while at worst, a certain piracy modchip team might make the first move.”
It’ll likely be some time before actual homebrew software is capable of running on the Switch’s operating system. Right now, unless you’re looking to install Linux on Nintendo’s console, the exploit isn’t particularly useful for the average user.
Getting the hack up and running also remains a complicated process at this point. It involves getting the Switch to run in RCM mode — a USB-based rescue mode for flashing Tegra devices that have been bricked — and then a USB-based exploit needs to be loaded on to the system. Back at the height of iPhone jailbreaking, this would also be referred to as a ‘tethered jailbreak,’ since this process needs to be performed every time the Switch is booted up.
“Since this bug is in the Boot ROM, it cannot be patched without a hardware revision, meaning all Switch units in existence today are vulnerable, forever,” writes Fail0verflow. The group goes on to outline the exploit’s process, which actually requires a wire bridge (or a 3D printed tool).
“As it turns out, what Tegra calls the Home button is actually connected to Pin 10 (the rearmost pin) on the right hand side Joy-Con connector. You can just use a simple piece of wire to bridge it to e.g. a screw on the rail (easiest), or pins 10 and 7 (or 1) together (10 and 9 won’t work),” writes the hacking group.
For more information on how the hack actually works, check out Fail0verflow’s in-depth explanation and step-by-step process.
It’s possible Nintendo could block the hack by altering the Tegra X1 processor. A new Tegra Processor with the name T214 is referenced in the Switch’s 5.0 firmware, along with a RAM bump to 8GB from 4GB. This means that it’s possible the Japanese gaming giant has plans to release a new version of the console that’s free of this hardware level exploit. That said, according to these hacking groups, all current Switch consoles are compatible with the exploit.
In a series of tweets, Fail0verflow showed off homebrew and various other games running on the Switch, including the Japanese version of The Legend of Zelda Windwaker being played on the GameCube’s Dolphin emulator.
In utterly, completely unrelated news, here’s a sneak peak at a totally brand new Zelda game coming soon to Nintendo Switch. pic.twitter.com/5FwyBX7L1y
— fail0verflow (@fail0verflow) April 23, 2018
ShofEL2 also supports running Switch homebrew. Technically. pic.twitter.com/pIcxvmsgPj
— fail0verflow (@fail0verflow) April 23, 2018
Source: Fail0verflow, Twitter (Kate Temik) Via: Eurogamer


