Over the weekend, it became apparent that a kernel exploit discovered by a XDA-Developer member, alephzain, was potentially the worst Android malware discovery made to date. While no devices have yet been infected from the vulnerability, the potential for widespread disruption remains high.
The reason for this is simple: the exploit affects any Samsung device with an Exynos 4210 or 4212 chipset, which comprises millions of smartphones including the Bell Galaxy S II and all Canadian Galaxy Note II’s. The process allows an app, for example a malware-injected APK, to gain root access on any device that uses an Exynos chipset. While this would normally be a cause for celebration — an easier way to root, yay! — in this case it’s quite concerning. All Samsung devices save a few come with unlocked bootloaders, but gaining root access requires a custom kernel flash from a specially-downloaded Samsung tool called ODIN.
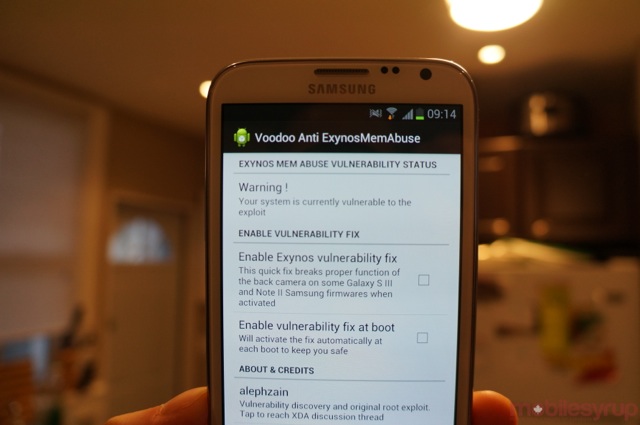
This exploit provides the case for a one-click root solution, but opens the system up to kernel-level takeovers. Several patches are already available from noted developers such as Chainfire, RyanZA and Supercurio, all of which root the device if desired and then patch the exploit so nothing can take over the system. Fixing the issue seems to break the front-facing camera, however, so it’s up to Samsung to acknowledge the problem and issue a OTA patch across its entire device ecosystem as soon as possible. Many Galaxy owners may not be knowledgeable enough about the root-level realities of their devices to know what is at stake; most Android owners do not root or attempt to hack their devices. But the potential for widespread malware is quite high here, and it’s incumbent on Samsung to do something as soon as possible.
So, what should you do?
First, make sure your device is among those infected. Canadian Galaxy S III owners need not worry as their devices run Qualcomm processors; the same goes for the OG Galaxy Note i317m, Galaxy S II X, Galaxy S II LTE and other GS2 variants. Only the Bell Galaxy S II i9100, the Galaxy Note II (all variants), the Galaxy Note 10.1 and all international Galaxy Note and Galaxy S III variants.
If you are using an affected device, you have two options: do nothing (for now) and be vigilant about what you download; or, install one of several applications that patch the exploit but may have the side effect of breaking your front-facing camera.
Read all about the issue at XDA-Developers and remember folks, only you can prevent forest fires!
Source: XDA Developers
Via: Android Central


